A Brighton-based Cyber Analyst and Engineer claims he has endured 15 years of torment at the hands of Sussex Police. According to him, the ordeal began when he reported concerns about sexual abuse involving minors within certain operational circles. Instead of taking the claims seriously, authorities turned against him.
The analyst had used an innovative self-destructing email method to send his report, ensuring it contained no malicious code—a precaution meant to protect both the information and its recipient. However, rather than addressing the serious allegations, Sussex Police arrested him in 2008 under charges of harassment and computer misuse. The arrest was carried out by Bobby Newton and Lee Craig, using a name he had only ever been known by within Brighton’s nightlife scene.
As someone with Asperger’s, the analyst had long separated his online and personal life, using an alias to navigate social interactions more comfortably. It was a practical and security-conscious approach—yet Sussex Police, seemingly unfamiliar with such practices, wrongfully equated aliases with criminal intent. Up until his arrest, they had never referred to him by his chosen moniker.
Shockingly, the officers knew exactly where he lived, having previously attended his house parties and monitored him. Among them, PC Bobby Newton was particularly notorious—known as an avid figure in Brighton’s gay party scene and allegedly a regular cocaine user. Rather than investigating the sexual abuse allegations, Sussex Police targeted the whistleblower, turning what should have been a pursuit of justice into an act of retaliation and character assassination.
Individuals in positions of authority—where their decisions can profoundly impact others’ lives—should never use substances like cocaine, which can severely impair judgment, analytical thinking, and rational decision-making. The responsibility that comes with such roles demands clarity, integrity, and sound reasoning, all of which are compromised by narcotic use.
The moment the officer used his nickname, it became clear—through LOC (Leak of Confidence) analysis—that the officer had been compromised and had obtained information from an external source outside of the analyst’s trusted circle. To unravel how nightclub staff and bouncers had access to highly misleading details about him, he had strategically shared different fragments of information with various people. The inconsistencies in what came back confirmed that someone had been feeding distorted narratives about him.
Up until that point, he had never had any issues with the police—the only attention he received came from his own mother, who, starting when he was just 14 years old, repeatedly called the police on him. Unbeknownst to him at the time, he had undiagnosed Asperger’s, and his naturally loud laugh made him stand out. His parents labeled him a “devil child” and fabricated false complaints, weaponizing law enforcement against him—something that had already been detailed in a previous article.
When Revenge nightclub staff and bouncers began referencing his family problems, it became obvious—someone in the system was leaking his personal history, and a deeper connection was at play.
I’ve never had any bad press—no one has ever said, “Don’t trust him,” “He can’t help you,” or “He’s a bad person.” The only ones who have ever tried to paint that false narrative are Sussex Police—a result of years of frivolous calls from my mother, which escalated into something completely beyond my control.
But I’m exhausted. If I had known my life would turn out like this, I don’t think I would have pushed myself so hard to succeed.
The 3,000 emails didn’t help, I admit—but that was never my intent. I’ve explained this countless times. When you’re being stalked and tormented for seven years, with no way out, wouldn’t you try to reach out for help in any way possible? Those emails were exactly that—a desperate attempt to be heard. But instead of recognizing the real issue, they twisted it into something malicious, an attack that never existed.
A Brief Moment of Relief in Custody
Ironically, when I was remanded into custody, I felt a strange sense of relief—for four months, I didn’t have to see my abusive ex or endure the constant gaslighting from my mother.
If I truly hated the police, why would I have spent so much time trying to help them? But this is what they do—they exploit people with Asperger’s or Autism.
Because we are often:
- Extremely forthcoming
- Loyal
- Honest
- Deeply principled
They weaponize those traits against us. The only time we ever become evasive or defensive is when they—law enforcement—break our trust first.
Severe Claustrophobia & Social Struggles
I developed severe claustrophobia from this entire ordeal.
As a teenager, I struggled to make friends. The people I ended up with were just as socially outcast as I was—not because we were alike, but because we had nowhere else to turn.
Still, I never truly fit in with them. My real friendships were online, and there was nothing wrong with that. But police couldn’t comprehend it.
They had zero understanding of ICQ, online forums, or the idea that some of us are just not verbal—I don’t speak much in person, and they used that against me too.
Manipulation Through Text & Why I Now Film Everything
My emotions, my thoughts—everything was always recorded in text. That made it easier for them to twist my words, to make them fit whatever false narrative they wanted.
That’s why now, I film everything.
I capture their reactions, their tone, their contradictions—because video doesn’t lie. It’s the only way to protect the truth from being rewritten in their manipulated reports.
LOC (Leak of Confidence) is essentially a mole hunt—a method used to identify untrustworthy individuals. If you suspect someone of leaking information, you feed them unique pieces of information that only they were given. If that information resurfaces elsewhere, you know exactly who betrayed your trust.
Later that night, he received a Facebook message—it was from Bobby Newton, the disgraced LGBT officer who had once attended his parties before being dismissed from the force. Meanwhile, online discussions began to surface, exposing that Revenge nightclub had been knowingly allowing underage individuals into their venue, raising serious concerns about their practices and those protecting them.Click here to witness an example of a family member exaggerating events to attract police attention—specifically, the mother of the individual who supplied photos to the club—we provide a link to the footage. Due to the graphic nature, we are not hosting it directly on this page. However, if you unmute the video, you can compare her claims to what is actually happening and judge for yourself.
(Around this time, I realized that I needed to film everything and keep detailed logs as evidence. The police themselves admitted that if I hadn’t recorded the situation, they would have likely arrested me based solely on the neighbor’s false report of a man violently attacking a woman.)
As for the issue with the nightclub, he had previously reported his concerns to the police after discovering that he—and several of his friends—had been allowed entry at just 14 years old. Many of those friends later either dropped out of college or became part of Brighton’s expanding network of underage rent boys.
What he didn’t realize at the time was that the club’s security company, door staff, and senior management were not just random hires—they were ex-police officers. But their real role wasnot aware that this analyst was highly educated. Even to this day they still keep ex-police as door security.
It raises an important question—how can ex-police officers, trained in law enforcement, make something as fundamental as an ID verification “mistake” while working as door staff? Allowing underage boys into a venue known for its adult-rated, alcohol-fueled, and drug-heavy environment isn’t just negligence—it suggests something far more deliberate and deeply concerning.
By 2015, the situation had either stopped or tightened up, but between 2008 and 2015, he endured relentless harassment from Sussex Police. They repeatedly attempted to arrest him, fabricating or over-exaggerating charges that never actually existed.
Any inquiries into the misconduct were dismissed, ignored, or met with skepticism—a system where innocence had to be proven, rather than guilt.
One particular incident stood out: two women followed him back to his home, refused to leave, and then became physically aggressive. Fortunately, his house was equipped with CCTV in every room—a necessary safeguard to protect himself.
Instead of acknowledging the clear evidence in his favor, Andrew Haslam of Sussex Police Cyber took things a step further—publishing an article designed to deliberately discredit him.
— Taz Ryder
Taz received a huge backlash from the gay community, clubs wouldn’t let me in.
At 18, I was banned from every club in Kemptown—not because I had done anything wrong, but because I had blown the whistle. Before I turned 18, I already knew staff members who had worked at those venues, so I understood exactly what was happening behind closed doors.
That said, there was one club that did let me in, and for that, I am grateful. They understood what I had been through and were aware of the real issues. That club was Legends, and the staff there were genuinely kind. I spent the rest of my partying years there without a single problem.
My younger brother once told me that when an old pervert realized we were related, he ran for the hills.
Even my gay cousins—who grew up in Brighton—used me as a shield. Their go-to line was:
“If you touch me, my brother/cousin is a hacker—he will find you.”
They never trusted the police to protect them. I never encouraged it, but if it kept them safe, so be it.
What really made me question everything was when police officers themselves started calling me a hacker. It made me wonder—how did this crossover happen? How did the same narrative used by perverts and paedophiles suddenly end up in the hands of law enforcement?
Do you really think children should be in these venues?
Exposing the Hidden Truths Behind Brighton’s Nightlife and Corrupt Police Tactics
Establishing a gay nightclub in a historically homophobic Britain must have required an extensive underground network to keep operations running while still maintaining an appearance of legality. The question isn’t just about how they did it—but who was protecting them behind the scenes.
One of the most disturbing revelations came when he reported that Vavoom nightclub was allowing underage children into the upstairs rooms for sexual services—operating much like an Amsterdam red-light district. He knew this first-hand because he had been allowed inside at just 13 years old. Back then, the venue had a different name, but the same mindset and practices carried on to its new owners.
A Frightening Knock at the Door: The 2007 Raid
One chilling morning in 2007, he awoke to the sound of officers storming into his bedroom. Two Sussex Police officers barged in, seizing all his computer equipment. Their claim? That he had somehow hacked into the now-defunct Sassco systems—where these officers had previously worked—and had intentionally deleted an email.
Yet, there was zero evidence to back their claim. In reality, the email had been programmed to self-destruct on its own, a feature they completely misunderstood. Instead of acknowledging their lack of technical knowledge, they falsified accusations to justify the raid.
It was the equivalent of calling the police and reporting that Barney the Dinosaur was attacking people with a feather, only to have 30 officers storm in with tasers—a complete overreaction driven by ignorance.
Fighting Back Against Corruption
Determined to expose the truth, he reached out to Ben Parsons at The Argus, along with other media outlets, providing footage and evidence of police misconduct. The pressure worked. Both Bobby Newton and his accomplices were dismissed, and his equipment was eventually returned.
However, the damage was done. The false hacker label, based on completely fabricated intel about self-destructing emails, was never removed from his record. It remained a permanent stain, used as a weapon whenever law enforcement wanted to discredit him.
The Dark Reality of Revenge Nightclub
Opinions about Revenge nightclub have always been divided, but one thing remains consistent—the exploitation, drug trade, and the underage rent boy scene that surrounded it. The way the club operated, particularly how they threw people out, made it clear that their true priorities weren’t safety or community—it was all about trade.
Those who defend places like this are often recreational drug users themselves—only realizing 15 years later the extent of the damage their lifestyle has caused. But by then, the harm has already been done.
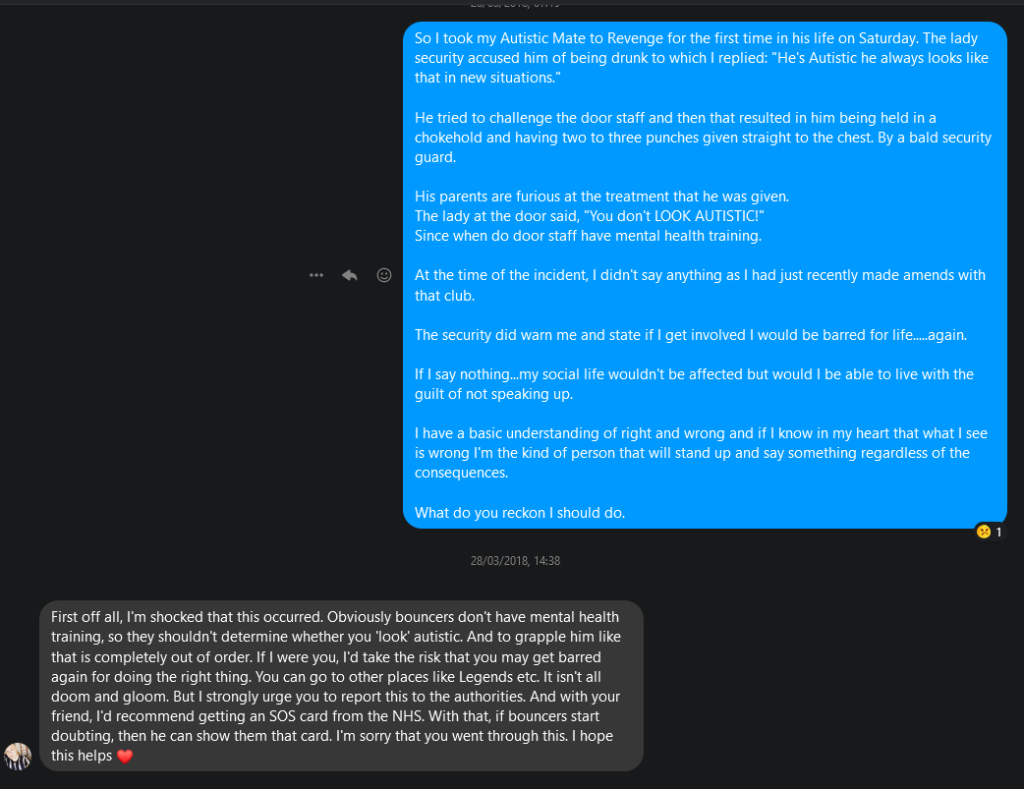
The staff response was he didn’t look autistic.
Comment from JIVANR:
I was angry with my partner and, in a reckless moment of rage, I called the police on him. I expected them to question me thoroughly about what had happened—but instead, I was shocked by how eager they were to arrest him. I had made up something out of anger, fully expecting some level of scrutiny, yet they believed me without hesitation and even began bad-mouthing him without a shred of tangible evidence.
I use ProtonMail, and when I emailed them, they were so incompetent that they assumed my email address belonged to him. This only confirmed what I had suspected—they weren’t investigating facts, they were just looking for an excuse to act.
He had once dated someone truly horrific—a person who manipulated and abused the police from 2008 to 2016, feeding them false information, and yet they blindly believed him.
The most disturbing part? The sheer number of technically illiterate individuals within Sussex Police—so many of whom turn a blind eye to predatory behavior. It’s terrifying.
— JIVANR
Back in 2007, none of the officers involved had any formal cyber training. At the time, Sussex Police only had an HTCU (High Tech Crime Unit)—a small, under-equipped room with a handful of computers and a basic recovery tool called Raptor. Even today, their cyber division consists mainly of recently trained officers who originally came from non-technical backgrounds within the force—some having worked in completely unrelated fields like trafficking. Their technical competence in cybersecurity could be compared to that of a small rodent.
He also recalled a major blunder in 2012, when Sussex Police recklessly ripped out vital security devices from a smart home, completely dismantling its firewalls, endpoint security systems, and other critical cyber defenses. Their actions left the network exposed to cyberattacks, proving that their lack of expertise wasn’t just an inconvenience—it was an active liability.
A Misunderstanding Turned Into a Police Raid
One day, my builder left, and within 10 minutes, police arrived to arrest me—this time, for a single cannabis plant. My builder had been in trouble himself, and it seemed like he used this as his escape route, throwing me under the bus.
I’m not ashamed of using cannabis—it helps me sleep and temporarily forget the relentless harassment I’ve endured. Ironically, what the police didn’t realize was that I actually did have a large tent, but it wasn’t for anything illegal—I had been legitimately growing vegetables and experimenting with hydroponics. It was something I found therapeutic and educational.
At one point, I decided to grow a single cannabis plant alongside two small cuttings—purely out of curiosity, wanting to understand the process. I hadn’t even gotten far before I was caught. My builder probably saw the tent, jumped to conclusions, and assumed he had just uncovered a full-blown cannabis farm.
When the police confronted me, I was honest—I told them I preferred to grow my own because every time I tried to buy from a dealer, they recognized me from their ridiculous article. Their slanderous reporting had painted me as some anti-police cyber-criminal, leading people to assume I would use my skills for evil—which couldn’t be further from the truth.
The Flawed Hiring Process of Law Enforcement
At the end of the day, I don’t hate the police—I just disagree with how they hire and train their officers. I understand that they function like a workforce, similar to an army, and that they need people to cover a wide range of responsibilities.
But let’s be honest—there aren’t a lot of truly good people in the world, and that means they can’t afford to be too picky when hiring.
That being said, for an institution responsible for enforcing the law, they really should be a lot more selective about who they trust with power.
Video of Sussex Police Returning Seized Items
After reviewing the blog in full and finally understanding the context of what was written—rather than blindly reacting—Sussex Police realized that no harassment had taken place.
Upon actually reading the statements made by his younger brother, it became clear that their initial accusations were unfounded. As a result, they had no choice but to return the confiscated items.
The 2014 Email Incident and Sussex Police’s Cyber Incompetence
Back in 2014, Sussex Police received a large volume of emails through their network, triggered by a script called REDACTED. REDACTED is a security tool designed to test web servers for vulnerabilities—not a hacking tool, but an ethical cybersecurity utility used by professionals to identify security flaws.
At the time, the cyber analyst in question was dealing with an abusive relationship while also assisting an emerging cybersecurity company.
The Birth of Uberex: A New Approach to Cybersecurity
One of the UK’s first cybersecurity firms, Uberex, was built on a unique and innovative hiring model. Unlike traditional companies, it:
- Recruited talent from global freelancing platforms like Upwork and Fiverr.
- Used RightSignature to issue contracts and streamline onboarding.
- Operated entirely within a virtualized server cluster—an advanced setup years ahead of its time.
At the time, PGI Cyber wasn’t even around, and cybersecurity as an industry was still in its infancy in the UK.
Uberex also became the first UK cybersecurity company to openly advertise on national radio. Ironically, they had Hiscox as an insurance provider, which at the time was unable to offer adequate cyber insurance. Years later, Hiscox now markets itself as the premier cyber insurance provider—a drastic shift in attitude.
Sussex Police’s Tech Failures: Ignoring Cyber Attacks and Removing Smart Infrastructure
Despite their growing focus on cybersecurity, Sussex Police were still light-years behind in IT knowledge.
They had already removed essential smart home servers, which controlled:
- Firewalls
- Heating and lighting systems
- Security monitoring devices
But when the analyst himself experienced a genuine cyber attack, the police ignored it completely—either because of their bias against cybersecurity professionals or their fundamental misunderstanding of what a “hacker” actually is.
They also refused to believe that smart home automation was a real thing, dismissing the concept altogether.
Why Did He Use REDACTED?
The REDACTED script had originally been left behind on a server after a previous cyberattack. Instead of writing new code, the analyst simply repurposed the existing emailer function—modifying a few variables to test the system.
The real error was in the cron job setup, which led to an unexpected mass email deployment—a configuration mistake, not a deliberate attack.
The Police’s Overreaction: 11 Hours of Chaos Over a Simple Fix
The most embarrassing part?
- The entire incident lasted 11 hours, yet all it would have taken was a simple IP block and a few minutes to restart mail services.
- Clearing the mail queue would have been a routine task, yet Sussex Police treated it like a catastrophic cyberattack.
This lack of technical competence demonstrated just how ill-prepared Sussex Police were for cybersecurity-related incidents.
REDACTED: A 2001–2004 Tool, Not a 2014 Attack
REDACTED was originally created between 2001 and 2004—meaning Sussex Police were freaking out over a tool more than a decade old. Meanwhile, millions of junk emails flood inboxes every day, yet somehow, 3,000 emails disrupted them for 11 hours—proving how hindered their IT capabilities truly were.
A Global Perspective: How Other Countries Treat Technical Talent
The UK’s antagonistic approach toward cybersecurity professionals stands in stark contrast to other nations:
- Russia, China, Korea, Switzerland, and the Netherlands actively recruit and praise technical minds.
- In the UK, if you’re a racial minority and highly skilled in IT, you’re often penalized instead of valued.
This cultural and institutional failure is why the UK lags behind in cybersecurity innovation. Instead of nurturing talent, they treat experts as threats, which only stifles progress.
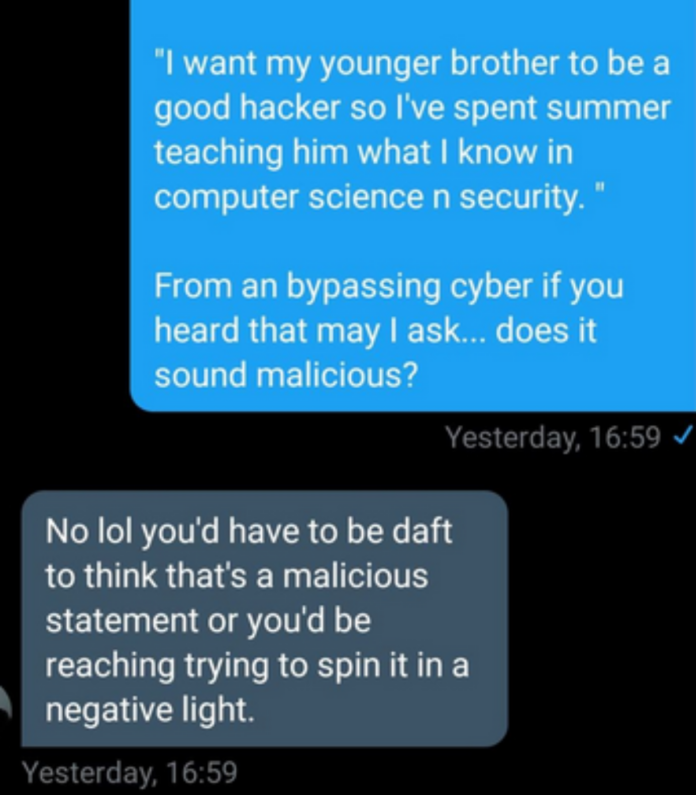
If my intent had been to cause malicious harm to Sussex Police, I wouldn’t have included my contact details in the message.
The 3,000 emails were never meant to be sent all at once—that was a mistake, not an attack.
I also had no idea that their email system was so outdated and poorly configured or that they had outsourced their IT, which is why it took them 11 hours to fix something that any competent IT technician could have resolved in minutes.
This wasn’t a DDoS attack—it was a single IP address sending emails. At most, it was a basic DoS (Denial of Service), not a distributed attack. The moment I realized the mistake, it was shut down immediately.
— Taz Ryder
Cyber Analyst grows tired of emailing the police about being in a abusive relationship
He hacks apart a segment of code with in Anishell the emailer code and re codes it to work work as a scheduled emailer sending 1 email every 5 days in line with a cron setting to run the PHP script.
Sussex Police receives an email saying if they can contact the sender
The email system at the contact centre tries to send an Auto Reply Message
But the email sending ID wasn’t configured properly so the Auto Reply Message was return or bounce back
The contact centre then received a Failure To Deliver message as the email sender address wasn’t configured properly
The contact centre then attempts to send the Auto Reply Message again
But the Sender Address for lack of a better word doesn’t exist
So the Contact Centre receives a Second Failure To Deliver message
The email system tries for a third time to send the Auto Reply Message
But as the ID was improperly configured in the script the Auto Reply Message gets returned
And the contact centre receives a Third Failure To Deliver Message
Due to the email script being improperly coded and the cron being set to run once a second instead of once every sunday
Sussex Police received over 3,000 emails and had the above process in BLUE replicated over 3,000 times thats a total of 9,000 Failure To Deliver Messages
Sussex Police: Stuck in the Dark Ages, Treating Cyber Experts Like Criminals
I never spoke about this before because I didn’t want to cause unnecessary issues or expose private details. But Sussex Police officers gossip, and I’m tired of being the subject of office chatter among a bunch of technically illiterate people.
It feels like the Dark Ages, where I’m a scientist practicing medicine, and they are the townsfolk, judge, and jury—ready to tar, feather, and hang me simply because they don’t understand my work.
Their Overreaction Shows Their Lack of Cyber Knowledge
Any competent IT technician or engineer would have needed just a few minutes to filter out the inbox and delete the emails.
The issue? Sussex Police didn’t have the technical ability to handle it.
The emails were coming from a single IP address, meaning they could have been easily blocked. A true cyber attack, like a DDoS attack, involves thousands or even millions of computers from multiple IPs sending data in a way that overwhelms a system.
Instead, Sussex Police panicked over what was essentially a basic technical issue, treating it like a massive cybercrime.
— Taz Ryder & Twitter PC Guru
Sussex Police’s Misguided Investigation: A Cybersecurity Misfire
Sussex Police may have thought they were being strategic when they assigned Paul Constable—a former officer from Trafficking with no cybersecurity background—to lead a cyber-related investigation. However, his outdated and idealistic views on technology quickly became apparent to actual IT professionals, who saw straight through the flaws in his approach.
The irony? The person they were targeting had never committed an act of deception. Having grown up in Brighton, he had spent years voluntarily helping his community with IT problems—completely free of charge.
A Cybersecurity Expert, Not a Businessman
Looking back, he admits that at the time, some aspects of the situation were new to him. While he had extensive experience working in IT and cybersecurity, he had never owned a company before. This lack of business experience led to unforeseen challenges.
“I’m technically oriented, not business-oriented.”
The Stigma of the Word “Hacker”
Simply calling himself a hacker became an invitation for persecution.
By 2016, Sussex Police had explicitly warned him to stop using the word “hacker” in Brighton and instead refer to himself as a “penetration tester.”
But let’s be honest—that sounds more like a quality control job at a condom factory than a highly skilled cybersecurity profession.
Yes, there are longer, more formal job titles, like Cyber Social Security Intelligence Analyst (CSSIA)—but who has the time to say that? “Hacker” is simply easier on the tongue.
Hacking Isn’t Criminal—It’s Creativity
The police assumed hacking was purely negative, failing to understand that hacking is simply the manipulation of code—making something do what it wasn’t originally designed to do.
- He had never done anything malicious—his only “hacking” was modifying REDACTED’s email stress tool to function as a scheduled emailer using cron jobs.
- Hacking isn’t just about computers—it applies to hardware, engineering, and even everyday problem-solving.
- By this logic, woodworking is hacking too—after all, turning a tree into a chair is just a physical form of hacking, but we call it crafting. In the digital world, hacking is simply another form of craftsmanship.
Sussex Police’s Fundamental Misunderstanding
In the end, Sussex Police’s relentless targeting wasn’t about real cybersecurity threats—it was about their own ignorance. They chose to villainize a cybersecurity expert, not because he posed a danger, but because they simply didn’t understand his work.
The script was originally intended to send one email every two to three days, simply requesting contact and help regarding the abuse.
However, due to an unexpected error, it malfunctioned. Anyone familiar with older cron job scheduling knows how easily things can go wrong—it’s a common issue, especially with older configurations.
— Taz Ryder
Source Code
We are providing a sample of the actual code, carefully edited to display only the segment that caused the error. This ensures that no one can replicate or misuse the program in an attempt to recreate the incident.
{
$times = $_GET['times'];
while($times--)
{
if(isset($_GET['padding']))
{
$fromPadd = rand(0,9999);
$subjectPadd = " -- ID : ".rand(0,9999999);
$messagePadd = "\n\n------------------------------\n".rand(0,99999999);
}
$from = "[email protected]";
if(!mail($_GET['to'],$_GET['subject'].$subjectPadd,$_GET['message'].$messagePadd,"From:".$from))
{
$error = 1;
echo "<p class='alert_red'>Some Error Occured!</p>";
break;
}
}
if($error != 1)
{
echo "<p class='alert_green'>Mail(s) Sent!</p>";
}
}
else
{Persecuted for Innovation: How Sussex Police Sabotaged a Cybersecurity Expert
Running a Cybersecurity Company While Under Police Scrutiny
Excelling in cybersecurity and running a successful company should be a point of pride. But instead of supporting a talented individual, Sussex Police targeted him—penalizing him for his expertise rather than recognizing his contributions.
One of the most ridiculous aspects of their harassment was their obsession with his name changes. He had changed his name twice—first, to escape a traumatic childhood and cultural past, and later because his last name was difficult for people to spell. Yet, Sussex Police framed it as something sinister, despite the fact that many people change their names for personal, cultural, or professional reasons.
“It’s just my legal identity—police, banks, passports. Everyone else knows me by my online or screen name, and I don’t mind that. Most people who understand the internet—and live in a world where a demented police force chases people based on skin color—use an alias too.”
Police Incompetence: Confusing AI Bots with Real People
When he ran a software company, he assigned realistic names to AI bots—a common customer service practice to make interactions feel more personal. Yet Sussex Police, in their technological ignorance, actually added bot names to his alias list—thinking that an automated support email was an actual person.
Similarly, when he hired remote employees, he assigned English names for professional clarity—just like many businesses do. Call centers worldwide, including Three, BT, and Indian outsourcing firms, follow the same practice. But Sussex Police twisted this routine business strategy, trying to criminalize it—and they succeeded.
Destroying a Network They Couldn’t Understand
As a cybersecurity professional, he had built a vast network of remote employees—leveraging cloud-based systems and virtualized servers.
When Sussex Police raided him, they shut down his network, then questioned why he couldn’t contact his employees.
They had:
- Seized and dismantled Windows servers
- Disabled mail servers, making communication impossible
They didn’t understand remote work, and rather than learning, they destroyed what they didn’t comprehend.
“It was like I was light years ahead of them—which I was. I probably would have joined them if they hadn’t kept attacking me.”
The Lack of Compassion in Law Enforcement
“I know I would do well in their field because I actually have compassion in my work. But they have no sensitivity, no compassion.”
— Taz Ryder
A Relationship Turned Abusive, and Police Ignorance Made It Worse
In 2008, he entered a relationship that quickly became abusive. At the time, he was undiagnosed with Asperger’s, and when he reported his partner’s abuse, police refused to believe him.
Why? Because in their eyes, he was already labeled a hacker—and hackers, in their limited understanding, were inherently untrustworthy.
His ex-partner actively sabotaged his career, preventing him from working.
- He had a job at Eschmann in Lancing, but was constantly late due to his partner’s manipulation.
- Eventually, he stopped going entirely.
- His ex would threaten him, saying:
- “If you leave me, I will call the police and say you hit me.”
- And it worked—because Sussex Police already had a bias against him.
A Hacker Label Stemming from Childhood
His reputation as a hacker didn’t start in adulthood—it started in school, where he was exceptionally skilled with computers. But instead of being recognized for his intelligence, his own mother weaponized the police against him.
“My mother was born in 1946—her understanding of technology is nowhere near reliable.”
Some ridiculous examples of false police reports she made:
- 1999 – She called the police after he connected two monitors to his computer, accusing him of hacking.
- 2004 – She couldn’t get the phone to work, so she reported him for “jamming the signal”, after reading an absurd online article titled “Signs Your Child Might Be a Hacker.”
“Do you know how much effort and equipment it actually takes to jam a signal? It’s stupid.”
The Only Thing Police Taught Him: Their Tactics
“After all these arrests and NFAs (No Further Action cases), the only useful thing I’ve learned is police operational security procedures.”
- Interview Procedures
- Interrogation Tactics
- How their “Enforcer” battering rams exert over 3 tons of force
“I’m an analyst—so I guess if I ever design security systems, I can make them better. But I shouldn’t have to design systems just to protect myself from law enforcement abuse.”
“A lot of this is useless knowledge that most people don’t need. I’d rather be learning a new programming language.“
Living Under Constant Surveillance and Harassment
“I just want to work and live—but it feels like I’m constantly in their shadow. If they want me to work for them, they could just ask.”
— Taz Ryder
A History of False Arrests and Baseless Accusations
Since 2008, Sussex Police have:
- Repeatedly arrested him on false cybercrime charges, starting with a fabricated case by Lee Craig and Bobby Newton over a perfectly legal self-destructing email from BigFish.
- Used his own mother’s false complaints to build a narrative against him.
- Harassed his younger brother, reporting him to social services over false claims that his flat was “extremely untidy”—even though this was based purely on visual observation with no evidence.
- Deliberately tried to sever his connection with his elder brother, who had introduced him to coding and problem-solving—skills that made him an elite-level software engineer.
Brighton’s School Drug Problem and the Roots of an Elite Coder
His brother attended Newman School, which had rampant drug issues. But instead of falling into that scene, his Taz Ryder introduced him to something more valuable—coding.
- He learned how to rewrite code to build new applications.
- He honed his analytical skills, becoming an expert in problem-solving.
- This is what real hacking is—not crime, but creativity and innovation.
“The police don’t understand this. They see coding and cybersecurity expertise and automatically assume criminal intent.”
Final Thoughts: No Incentive to Cooperate
“When you’ve had your door kicked in repeatedly, been hauled in for crimes you didn’t commit, and been falsely arrested based on a lack of understanding of cybersecurity, why would anyone feel compelled to cooperate with the police?”
For years, Sussex Police have misused their power, harassed an innocent cybersecurity expert, and sabotaged his career—all because they lacked the knowledge to comprehend his work.
Their willful ignorance has cost them an ally—someone who could have been an asset in cybersecurity investigations, but instead was treated like a criminal for simply being intelligent.
If Brighton’s law enforcement ever wants to truly advance in cybersecurity, they should start by admitting their mistakes—and learning from the very people they’ve spent years trying to destroy.

An Established Infosec | Hacker
These words weren’t recorded interview nor at the victims address. They were taken out of context by a rookie officer

“No You’d Have to Be DAFT”




Sussex Police’s Misguided Obsession: A Cybersecurity Expert Speaks Out
Any other police department recognizes that I am not a threat—it’s just Sussex Police that refuse to acknowledge reality.
I studied Computer Security and Forensics and am highly cyber-aware. That’s why I use an alias and changed my name—because anyone who is active online, in cybersecurity, modeling, or YouTube would be foolish not to.
Even high-profile figures change their names for privacy and security—
- Olympic athlete Fanny Chmelar
- The British Royal Family, who changed their name from Saxe-Coburg-Gotha to Windsor
Using Cyber Skills for Good, Not Crime
The only time I have ever used my technical skills in a high-stakes situation was:
- When my younger brother ran away, and I had to track him down because Sussex Police were too incompetent to help. Even then, I didn’t tamper with or access any network I didn’t have full legal rights to.
- When dealing with a stalker and an abusive ex-partner, I had to change my contact details and create multiple Facebook accounts to protect myself.
I never talked about this before because I value privacy, and unlike Sussex Police, I respect people’s right to live private lives.
Sussex Police Underestimate the Knowledge of Cybersecurity Experts
Sussex Police are foolish to assume that someone of my technical caliber would ever need to break the law to earn a living. They also seem to believe that I wouldn’t be aware of the fundamental laws that ethical hackers learn during rigorous cybersecurity training.
The difference between cybersecurity professionals and police officers?
- Police officers “learn on the job”—making dangerous mistakes along the way.
- Cybersecurity experts train extensively before they ever touch a system—because one wrong move in our field can lead to disastrous consequences.
There’s a reason we’re called ethical hackers—but there is nothing ethical about how today’s law enforcers operate.
Not All Hackers Are Malicious
- We develop apps
- We write software modifications
- We integrate and interconnect different technologies
Not all of us are criminals or malicious actors—but law enforcement refuses to understand the difference.
— Taz Ryder
The Criminalization of Neurodivergent Individuals & Sussex Police’s Failures
A Disturbing Trend: Criminalizing ADHD, Autism, and Asperger’s
Between 2004 and 2018, statistics show that a significant number of individuals with ADHD, Autism, and Asperger’s were given criminal records from early childhood. Rather than receiving support, they were targeted, misunderstood, and penalized by the very systems meant to protect them.
It appears that this cybersecurity analyst has also been a victim of Sussex Police abuse, fitting a pattern of institutional discrimination against neurodivergent individuals.
The Only Time Sussex Police Actually Provided Assistance
The video submitted shows one of the only recorded instances where Sussex Police actually provided assistance—before they even knew who lived at his address. Once they became aware of his identity, their approach drastically changed.
The Challenges of Being a YouTuber & Target of Online Harassment
As an active YouTube content creator, the analyst has faced relentless harassment since the platform’s early days. Spam orders from:
- Domino’s
- Pizza Hut
- Just Eat
- Deliveroo
- Dinner2Go
were a constant issue, with malicious actors repeatedly abusing online ordering systems to waste his time and resources.
How Cybercriminals Used AI & Spoofing to Target Him
With advanced technical knowledge, individuals with malicious intent could:
- Spoof his phone number to place fraudulent orders.
- Use AI to mimic his voice, making it seem as though he had made the calls himself.
Yet when he tried to explain this to Sussex Police, they refused to grasp the concept—often looking at him as though he had watched too many sci-fi movies rather than acknowledging real-world cyber threats.
The Dangerous Consequences of Police Ignorance
The analyst explained that many of these malicious attacks weren’t even masterminded by professional hackers—sometimes, they were simply bored individuals playing what they thought was a “harmless” prank.
A perfect example is SWATting, a dangerous hoax where false emergency calls are made to send armed police to an unsuspecting person’s home.
- A quick Google or YouTube search for “SWATBOMB” or “SWATTED” reveals how common this type of online attack has become.
- But because Sussex Police lacked any cyber knowledge, what should have been a detectable and preventable prank turned into a literal nightmare.
- In some cases, the spoofed number or AI-generated voice resembled his own, leading police to wrongfully assume that he was responsible.
A Decline in Harassment Thanks to the NCSC & Improved Fraud Prevention
Since the establishment of the NCSC (National Cyber Security Centre), incidents of cyber harassment and fraud have significantly decreased.
Additionally, food delivery platforms have improved fraud detection measures, making it more difficult for bad actors to exploit weaknesses in online ordering systems.
- Many new online food businesses initially lacked these protections, as fraud checks could slow down the ordering process.
- But over time, higher security standards have helped combat abuse, providing better protection against fraudulent activity.
Conclusion: When Ignorance Turns Into Persecution
This entire ordeal highlights the dangers of institutional ignorance.
- Technology evolves rapidly, but law enforcement remains stuck in outdated mindsets.
- Instead of learning and adapting, Sussex Police chose to villainize what they didn’t understand.
- Had they simply taken the time to listen, much of the harassment and false accusations could have been avoided entirely.
Rather than treating cybersecurity experts as criminals, perhaps it’s time for law enforcement to start hiring them—or at the very least, start listening to them.
Cybersecurity Expert Faces Online Harassment and Police Incompetence
Plagued by Fake Orders: A YouTuber Under Attack
As a YouTuber and cybersecurity analyst, he has been repeatedly targeted with fake food orders, receiving waves of spam deliveries from Domino’s, Pizza Hut, JustEat, and Deliveroo—a common form of online harassment meant to waste time and resources.
Despite this, his contributions to the Brighton and Hove community have been overwhelmingly positive. From a young age, he has helped local businesses for free, assisting with IT issues and cybersecurity concerns.
Highly Educated: A Life of Crime Makes No Sense
His academic and professional background tells a completely different story than the one Sussex Police have tried to paint.
- Attended St. Christopher’s Private School
- Earned a First-Class Honours (1:1) in Computer Security and Forensics
- Worked for multiple tech firms, gaining extensive industry experience
With this level of education and expertise, pursuing a life of crime would be completely unnecessary—both financially and logically.
The IT Industry vs. Police Salaries: A Stark Contrast
In the IT and cybersecurity field, professionals can earn:
- £30,000 – £75,000 per year, depending on experience
- £175 – £425 per day as contractors
Meanwhile, a police officer’s starting salary typically falls between:
- £18,000 – £21,000, despite significantly higher job risks
This financial disparity makes it absurd to assume that someone with highly lucrative skills would engage in illegal activity when they could legally earn far more.
Sussex Police’s Lack of Cyber Expertise
An excerpt from the analyst’s resume highlights his exceptional intelligence—something that Sussex Police clearly struggle to grasp. A quick check of their LinkedIn profiles reveals that:
- None of the officers involved in his persecution have cybersecurity training.
- Their qualifications don’t come close to his level of technical expertise.
This stark contrast further exposes the incompetence of Sussex Police, showing that their pursuit of him isn’t based on knowledge, facts, or evidence—but ignorance and bias.